WE ARE YOUR
TECHNOLOGY
PARTNERS
Streamlining your communication need with cutting edge solutions
tailored to your business so that you can focus on what matters most









Solutions tailored for you.
We are the independent and trusted managed service provider for the SME market in the South East.
Offering an invaluable depth of technical knowledge from a team of highly accredited experts, backed by many years of industry experience across IT solutions and services, Cloud Telephony Solutions, Business Mobile and both Physical and Cyber Security services.
Empowering organisations through technology
Selecting the right MSP to parter with has never been so crucial to a businesses success. We have the tools and solutions available to help you focus on what matters most.
Why not find out how we can help you achieve your goals.
-
![Google logo followed by the words "Baruch College" in gold text.]()
Steph Izzard
We're really happy with the service we receive from RJ Cortel; always prompt, polite and looking to go above and beyond for their customers.
-
![Google Review]()
Claire Leadbetter
RJ Cortel have been excellent in providing advice, technical support and good quality computer systems and programs to me over the years. I am very happy with them and will remain a customer for the foreseeable future.
-
![]()
Simon Moss
I have been a client of RJ Cortel for over 2 years, our business is a law firm, and the team at RJ Cortel have never let us down. They respond to support requests far quicker Read More
-
![Google logo followed by a five-star rating]()
Raanan Berlad
RJ Cortel are providing IT support to our firm. They are professional respond promptly, keep you informed and are pleasure to work with. Highly recommended.
-
![Google logo followed by a five-star rating]()
Kathy
Amazing service from a team we were lucky to be signed up to. Where other providers said the matter could not be completed in time to meet a deadline, RJ Cortel (Dave) came up trumps. We were told 2 weeks by Open Reach to Read More
-
![Google logo with five gold stars indicating a five-star rating.]()
Simon Haizelden
We have recently joined Cortel, they have been a pleasure to deal with from the original enquiry to the onboarding from our existing IT supplier and installing our new phone software. Everything has been dealt with in a very prof Read More
-
![Google logo with five gold stars indicating a five-star rating.]()
Calum MacInnes
RJ Cortel has proved to be a very helpful and important partner for our business. We would strongly recommend them and have found the people who work there to be friendly and capable and given us great peace of mind.
-
![Google logo with a five-star rating underneath]()
Mark Segal
RJ Cortel seamlessly switched our telephony to VOIP.
They are also providing us with IT support.
They always respond promptly to any queries and are knowledgeable and friendly. Certainly one of our most Read More -
![Google logo followed by a five-star rating.]()
Josh Imber
From start to finish the team at RJ Cortel had such high attention to detail when I purchased and had some equipment installed. I felt the project was managed expertly throughout by a very trustworthy group. Having found out Read More
-
![Google logo followed by five gold stars]()
-
![Google logo followed by five gold stars, indicating a five-star rating.]()
Abbi Lampard
I could not recommend R J Cortel and more importantly Dave Travers enough. We have just relocated our office into a retail premises and he has helped with EVERYTHING from the outset. Not only did he undertake all the telecoms work Read More
-
![Google logo next to a five-star review rating]()
Tim Luckin
I would highly recommend RJ Cortel. My firm have been using their service for over 8 years, they provide great products and excellent customer service to back it up.
-
![]()
Dale Pillay
Great Service! Good prices! awesome after sales!
The Latest News
In this article, we discuss the differences between Azure Virtual Desktop and Windows 365 in regards to cost, management and user experience, and some ideal use cases for both.
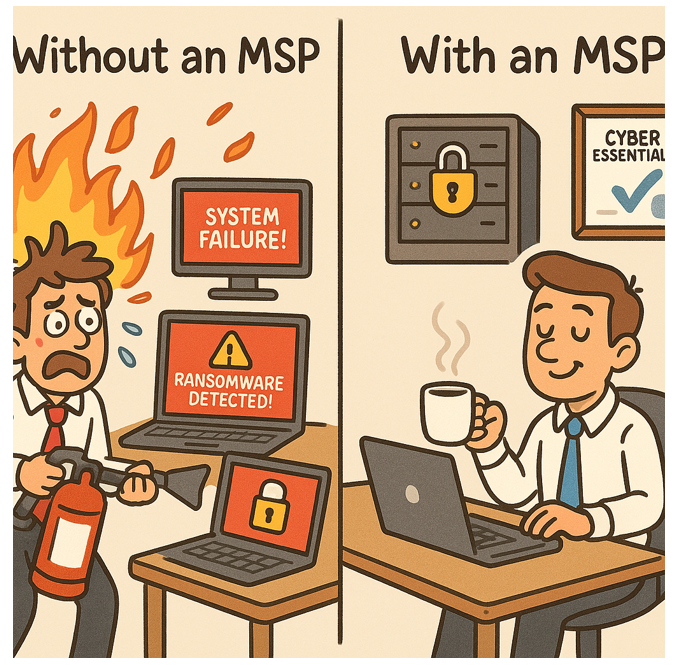
Sometimes we get called in when things are already on fire—servers down, ransomware in play, backups that don’t actually back anything up.
But the real magic happens before the fire starts.
We grabbed five minutes with Dave to discuss everything MSP. Read on to find his insights and recommendations.
Welcome to RJ Mobile!
Providing cost effective mobile plans to keep your business connected.
In today’s fast-moving business world, technology is no longer a “nice to have” — it’s the backbone of how SMEs in Sussex, Kent, and Surrey operate. Whether it’s safeguarding data, supporting remote teams, or enabling smooth customer experiences, your IT systems need to run flawlessly.
For any forward-thinking business, investing in a sound technology strategy is one of the best ways to ensure long-term prosperity. But, recruiting personnel for your IT department can be expensive and tricky and often ends up costing far more than it’s worth for your company. There is, however, another option — Managed Service Providers (MSPs).
The cloud is one of the most important considerations for any modern company. After all, the power that the cloud provides is second to none and can facilitate lots of different tools that can supercharge your business.
Your business’s network security is one of its most important considerations. After all, protecting your network is like protecting the physical building of your business itself — attackers can cause damage, steal important information, and even cripple your business in the long term.
Artificial intelligence is here, and is a major consideration for any business. With 83% of companies stating that AI is a top priority in their business plans, knowing the best AI tools available at your disposal is important for your business’s long-term success.
The transformative power of artificial intelligence (AI) is no longer a futuristic concept; it’s a present-day reality that is reshaping industries across the globe. According to McKinsey, over three-quarters of organisations are now using AI in at least one business function, with 55% reporting that using AI has led to revenue increases.
One of the most important aspects of how you interact with customers is the experience that you provide them. In fact, studies show that 79% of customers would switch to a competitor if they found out that said competitor had a better customer experience.
Cyber security is one of the top concerns for businesses today, and for good reason. With over 2,000 cyberattacks occurring every day worldwide, there is a genuine threat lurking around every corner.
With the rise of hybrid work and cloud-based operations, organisations today face an increasing number of cybersecurity threats that target vulnerable endpoints. Securing endpoints, such as laptops, phones, tablets and more, has never been more important.
One of the great aspects of the cloud is that it is possible to have unlimited scalability. With this being said, your Microsoft 365 subscription includes a base capacity of storage, and once it is met you will either need to pay to increase the limit or delete data to be under the limit.
As the cybersecurity landscape becomes more complex, security professionals are constantly looking for ways to create a ‘future-proof’ cybersecurity strategy.
As businesses continue to embrace remote and hybrid work models, finding the right virtual desktop solution is more important than ever. These cloud-based tools allow users to access their Windows desktops from anywhere in the world.
In the modern digital world, businesses need more than basic IT support to stay competitive. Managed Service Providers (MSPs) have evolved beyond their traditional roles, offering strategic guidance, advanced cybersecurity, and innovative technology solutions.
Microsoft 365 Copilot can revolutionise the way we work, offering a powerful suite of AI-driven tools designed to boost productivity and streamline workflows. From generating content and automating tasks to providing intelligent and actionable insights, Copilot is a useful companion for any business area.
In today’s digital world, data is the lifeblood of modern businesses. From customer information and financial records to intellectual property and operational data, keeping this information safe and intact is key.
The rapid pace of technological advancement has created an ever-increasing demand for software solutions across all sectors.
A migration to the cloud promises a whole host of benefits, such as reduced costs, increased agility and better scalability. The potential for improved efficiency and innovation is a powerful draw for organisations of all sizes.
Top talent drives business success. But in today’s competitive market, attracting and retaining those high performers hinges on one critical factor: employee engagement.
Email is a ubiquitous tool in the modern workplace, with up to 81% of people still using it as their primary method of communication. It’s no surprise that email is such a target for cybercriminals, with 3.4 billion phishing emails being sent every day.
In this tough macroeconomic environment, with high interest rates and the looming threat of recession, innovation and cost reduction are crucial for survival.
AI companions, such as Microsoft Copilot, are transforming the way we work. In fact, 70% of users say that Copilot increases their productivity, while 68% observe a significant improvement in the quality of their work when using it.
The promise of improved agility, scalability, and cost-efficiency draws organisations of all sizes to migrate to the cloud. However, cloud migration doesn’t come without its risks. As many as 1 in 3 migrations fail to reach their targets – and we believe a core reason for this is the lack of focus on post-migration.
Cybersecurity is quickly becoming one of the top concerns for businesses across the world, and for good reason. The risk of cyber-attacks has never been higher. 50% of businesses say they’ve recently fallen victim to a cyber threat, while 64% expect an attack in the future.
As your business grows, it can be difficult to keep track of the specific needs of your customers. After all, with a larger business, you’ll have more customers — all with specific needs and wants that you’ll need to remember to stay successful. Remembering everything can seem overwhelming, but there is a solution that you can implement to make life way easier.
Artificial intelligence is one of the most important technologies in the world right now. After having taken the world by storm over the past couple of years, every company wants to integrate it into their business. And, Microsoft has given companies the perfect tool to do exactly that with Copilot.
Virtualisation is a key factor in modern business strategies. After all, being able to run applications and desktops virtually makes your company more flexible and agile, and allows you to save costs and improve your company’s security all around.
Blog Posts
Contact Us
Interested in working together? Fill out some info and we will be in touch shortly. We can’t wait to hear from you!